T1563.001 - Gather Victim Identity Information: Credentials
Tactic: Reconnaissance
Platforms: Pre
Before weaponization and the creation or acquisition of a malicious payload, a key step in Lockheed Martin’s Cyber Kill Chain is reconnaissance. Reconnaissance is a critical practice in cybersecurity both for offensive and defensive purposes. Good reconnaissance can make or break a successful hack or pentesting attempt because it sets the stage allowing one to understand a target on a much deeper level. Due to the various avenues and methods that are available for a hacker to carry out recon, in cybersecurity, we usually categorize it into two distinct types: passive recon and active recon. Of the two, passive is much more effective if the adversary doesn’t want to draw any attention to him or herself as it involves collating data about a specific target without ‘actively’ engaging with it. It is pretty hard to protect and defend against recon, though you can put the effort in to make things more of a challenge for the bad guys. It is always a good idea to utilise relevant search engines to search through what data other users could potentially collect or collate about you so that you can then remove it. Through OSINT, data can be gradually gathered, leveraging a myriad of online resources that are free and publicly available.
Via the image below we can see that passive reconnaissance doesn’t just involve browsing various sites via the web. There are also real-life scenarios to consider where useful information could be divulged such as via dumpster diving and of course social engineering.
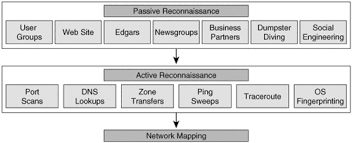
After passive reconnaissance, comes active reconnaissance. As the name suggests, this process is a lot more involved when compared with the former. The phase is essential for understanding a target’s specific vulnerabilities and possible attack vectors. As you can see from the previous screenshot, there are several ways that active reconnaissance can be carried out including via:
- Portscans (e.g. with Nmap )
- DNS lookups (nslookup )
- Zone Transfers
- Ping sweeps (with fping)
- Traceroute
- OS fingerprinting (can also be passive)
The goals of active reconnaissance include vulnerability identification (e.g. with Nessus), service enumeration (e.g. with SNMPwalk ) and network mapping (understanding a target network’s topology).
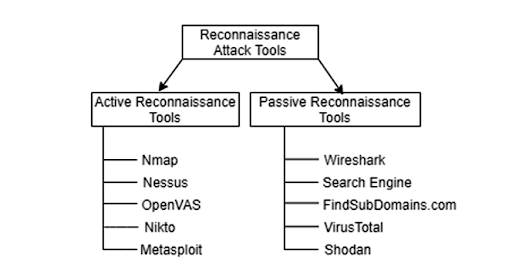
Because active reconnaissance involves directly interacting with a target or system via traffic, it can be logged and detected by security systems. Later on, we will look at specific methods that we can use on the defensive side to harden systems and prevent active reconnaissance from being as effective.
Due to the increased proliferation of social media and personal accounts now available on the web, there are many more avenues of attack that an adversary may choose to take to carry out reconnaissance duties and gather credentials for later use. For example, credentials can be gathered by carrying out sophisticated social engineering attacks using social media platforms, via phishing attacks or by leveraging databases of passwords already hacked and available for sale on the dark web.
Why is Credential Harvesting Important?
Credential harvesting is a critical step in many cyber attacks. By obtaining valid user credentials, attackers can:
- ->Bypass security mechanisms that rely on authentication.
- ->Escalate privileges within a network.
- ->Move laterally across different systems and services.
- ->Maintain persistent access to the compromised environment.
Practical Tutorial: Simulating Credential Harvesting
This tutorial is for educational purposes only. Unauthorized access to systems, data, or networks is illegal and unethical. Always obtain explicit permission before engaging in any security testing or credential harvesting activities.
Tools and setup:
To simulate credential harvesting from social media, we will use the following tools:
- Python : For scripting and automation
- BeautifulSoup : For web scraping
- Selenium: For automating web browser interactions
- Tor: For anonymizing internet traffic
Ensure you have Python installed on your system. You can then install the required Python libraries using pip:
$pip install requests bs4 selenium1. Setting Up the Environment
Firstly, set up a virtual environment for your project to keep dependencies isolated:
$python -m venv credential_harvesting
$cd credential_harvesting
$source bin/activate # On windows use .\Scripts\activate
2. Install Tor
Download and install the Tor browser from the official website: Tor Project
3. Configure Tor with Python
Install the pytorctl package to control Tor:
$pip install stemStart the Tor service and make sure it is running. On most systems, you can do this using:
$service tor startHint: For Windows systems, the below command can initialize tor.exe from the command line or PowerShell and your equivalent directory:
PS C:\Users\L2H\Desktop\Tor Browser\Browser\TorBrowser\Tor> .\tor.exe
4. Scraping Social Media for Credentials
We will use Python to scrape social media platforms. Note that scraping many social media sites is against their terms of service. Always check and comply with the legal and ethical guidelines.
Below is an example of how to use Selenium to scrape a social media site like Twitter:
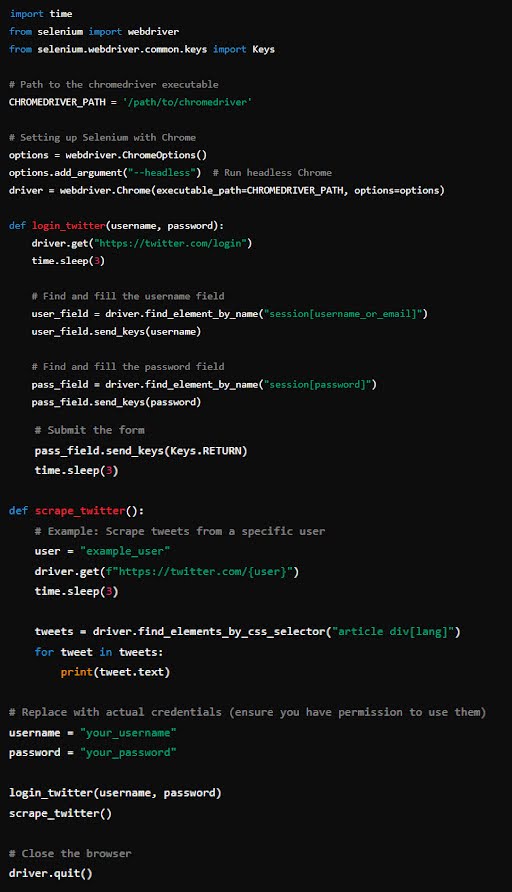
5. Using BeautifulSoup for Parsing
If you have access to HTML content (e.g., from an API or a previously saved file), you can use BeautifulSoup to parse it:
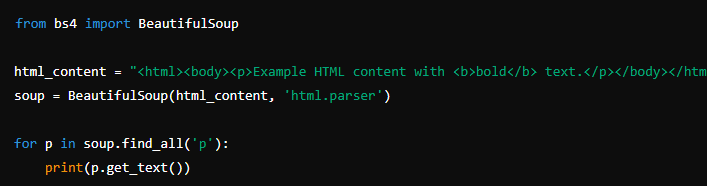
6. Anonymizing Traffic with Tor
To route your scraping traffic through Tor, configure your HTTP requests to use the Tor network. Here’s an example using the requests library:
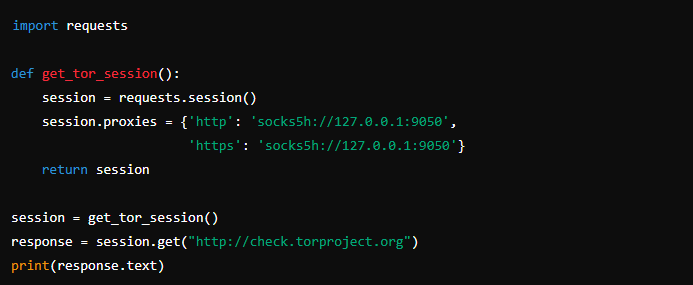
Additional Techniques:
- Phishing Campaigns
- Social Engineering
- Open Source Intelligence (OSINT)
Credential harvesting can also be achieved through phishing campaigns. This involves creating a fake login page that mimics a legitimate service to trick users into entering their credentials.
Social engineering is a psychological manipulation technique used to trick individuals into divulging confidential information. This can be combined with credential harvesting to increase the effectiveness of the attack.
OSINT involves gathering information from publicly available sources such as social media, online forums, and public records. Attackers can use OSINT to gather information about their targets, including email addresses, job titles, and personal interests, which can be leveraged in phishing campaigns or social engineering attacks.
Tools such as search engines, social media platforms, and specialized OSINT tools (Maltego) can be utilized to collect and analyze information about potential targets.
OSINT can provide attackers with valuable insights that help tailor phishing emails or social engineering tactics to increase the likelihood of success.
Organizations can mitigate the risk of OSINT-based attacks by educating employees about the importance of safeguarding personal information online and implementing security measures to detect and prevent unauthorized access to sensitive data.
Defensive Measures:
Along with many other reconnaissance activities, the mitigation of T1589 is challenging due to the technique being based on behaviors performed outside of the scope of enterprise defenses and controls. Nonetheless, various efforts can help to reduce the effectiveness of this attack method through the minimization of available data to adversaries.
The below measures should be employed in a ‘defense in depth’ manner to help make it as hard as possible for reconnaissance of credentials to be carried out:
- User training and awareness
- IAM (Identity and access management)
- Email security
- Network security
- Endpoint security
- Monitoring and logging
- Data protection
- Access controls
- Incident response
- Threat intelligence
- Educate employees about phishing attacks, social engineering and the importance of protecting personal and corporate identity information
- Implement strong password policies requiring complex passwords and regular updates
- Use MFA to add an extra layer of security
- Enforce the principle of least privilege
- Utilize email filtering solutions to detect and block phishing emails and other malicious content
- Implement DMARC, DKIM and SPF protocols
- Monitor and block suspicious activities using firewalls, IDS/IPS and other network security devices
- Use antivirus, anti-malware, and EDR tools to detect and mitigate threats
- Regularly update and patch all endpoints
- Use SIEM systems to correlate logs and generate alerts on suspicious activities
- Encrypt sensitive data both at rest and in transit to protect it from unauthorized access
- Implement DLP solutions
- Use privileged access management solutions to secure, control and monitor access to critical systems
- Develop and maintain an incident response plan that includes procedures for responding to identity information-gathering attempts
- Subscribe to threat intelligence feeds to stay informed about the latest TTPs used by threat actors
Case study:
In May 2024, Spanish bank Santander experienced a cyber attack from a hacking group known as ‘ShinyHunters’. The group is a black-hat criminal organization believed to have formed in 2020 and has conducted many data breaches against well-known organizations such as AT&T, Microsoft and Tokopedia.
For more info on the group, see SOCRadar’s ShinyHunters profile via: https://socradar.io/dark-web-profile-shinyhunters/.
As with many previous attacks, after the Santander hack, the adversary listed millions of compromised bank account details for sale on the Dark Web (sold in bulk) including account details, account numbers, balances and credit card numbers.
The group went so far as to offer Santander’s whole database for £1.6 million to a one-time buyer noting that Santander is very welcome to buy back their data if so inclined.
For initial access into company networks, ShinyHunters have previously sent phishing emails to company employees, enabling the theft of log-in data and access information.
If just one employee mistakenly clicks on a phishing link, then organizations can be at risk from similar attacks.
To help prevent cases like this involving the theft of sensitive data, data must be encrypted. Additionally, if working with third parties concerning the storage of data, third-party vendor risk assessments are recommended.
Further reading:
